Hacker Finds Way To Unlock and Drive Any Kia With Only the License Plate Number
Two years ago, "Kia Boyz" made waves with their TikTok challenge after people discovered how easy it is to start the engine of most Kia and Hyundai models. This was possible because many Hyundai and Kia cars built in the US between 2011 and 2021 lacked an electronic immobilizer. The discovery caused enormous problems for Hyundai and Kia owners, and it's still a black stain on the reputation of the two Korean carmakers.
What's worse is that teenagers still break into Hyundai and Kia cars, even though driving off without a key is impossible. Insuring a Hyundai or a Kia is also complicated, with some companies reportedly refusing to cover theft risk for these vehicles. To make matters worse, Kia and Hyundai were among the brands recently added to the infamous "Game Boy" key emulator's database, making stealing one a breeze.
Unfortunately, security problems are not over for the Koreans. A white-hat hacker recently discovered a serious vulnerability in Kia's dealer system that allows attackers to take control of any Kia using only the license plate number. Of all the car security problems I've written about, this is the scariest because it can be carried out without access to the key fob or even the vehicle. Thankfully, the vulnerability has already been patched, as Kia was informed about it before it was made public.
Sam Curry, a security researcher / white-hat hacker, made the discovery with one of his pals while probing Kia Connect, the app that remotely controls many of the car's functions. Owners use this app every day to lock/unlock and start their vehicles or just check on their status and pre-condition it before departure. Curry discovered that how the Kia Connect app communicates with the Kia servers to send commands to vehicles has a big problem.
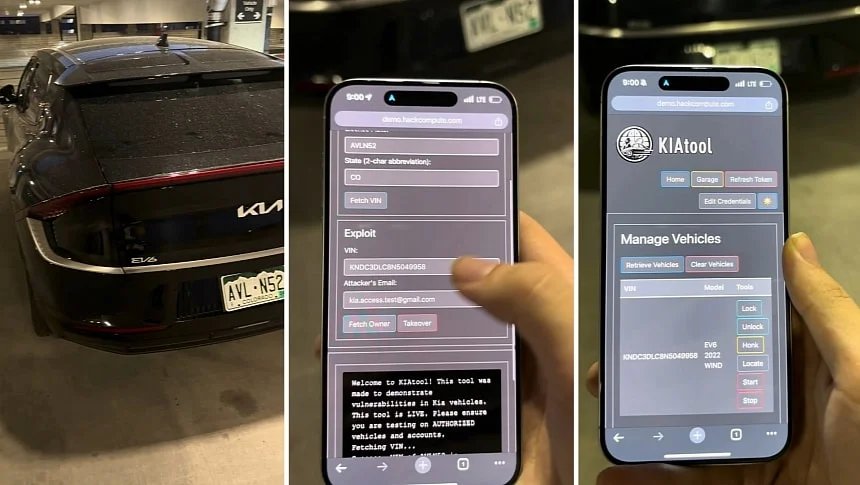
More specifically, Curry exploited a method that Kia dealers use to assign new cars to owners using Kia's KDealer platform. The vulnerability allowed him to impersonate a Kia dealership trying to register a customer's vehicle. To get control of the car, Curry needed its VIN, but this is readily available if you know where to look. He designed a tool that uses a third-party API to match the victim's license plate number with its actual VIN. This was all needed to get remote access to the compromised vehicle.
The worst part? Curry's tool worked with every Kia model produced over the last decade. The hacker not only has access to your vehicle in seconds but also your private information details. These include the name, phone number, email address, and vehicle location. The attacker can also add themselves as an invisible second user on the victim's vehicle without their knowledge. On some Kia models, Curry's tool even allows remote access to the vehicle's cameras.
Even though the vulnerability has been patched, it still casts a dark shadow over Kia/Hyundai security practices. It also proves that any device connected to the internet is as secure as the weakest link in the chain. In this case, the people discovering this issue were ethical hackers who first wanted to see it solved before revealing it. However, in other cases, bad people can take advantage of such vulnerabilities.